The Password Problem Isn’t What You Think
For years, cybersecurity professionals have told users to create complex passwords with upper and lower case letters, numbers, and special characters, and to change them every 90 days. The result is endless resets, sticky notes, and weaker security.
In July 2025, NIST quietly published the newest version of its Digital Identity Guidelines, SP 800-63-4, which officially rewrites that rulebook.
What Changed in NIST 800-63-4
NIST’s updated guidance modernizes authentication for today’s hybrid and cloud-first environments. Here are the most important updates:
- Password Complexity Reconsidered: Arbitrary composition rules are discouraged. Simplicity and memorability now outweigh forced complexity.
- Breach-List Checking: Passwords must be screened against known compromised lists.
- Longer Passphrases: Security strength should come from length and entropy, not character tricks.
- Elimination of Forced Rotation: Users should not be required to change passwords unless there is evidence of compromise.
- Multi-Factor and Passwordless Emphasis: FIDO2, passkeys, and device-based authentication are now first-class methods of verification.
INFO — Usable security is secure security.
NIST SP 800-63-4 § 5.2
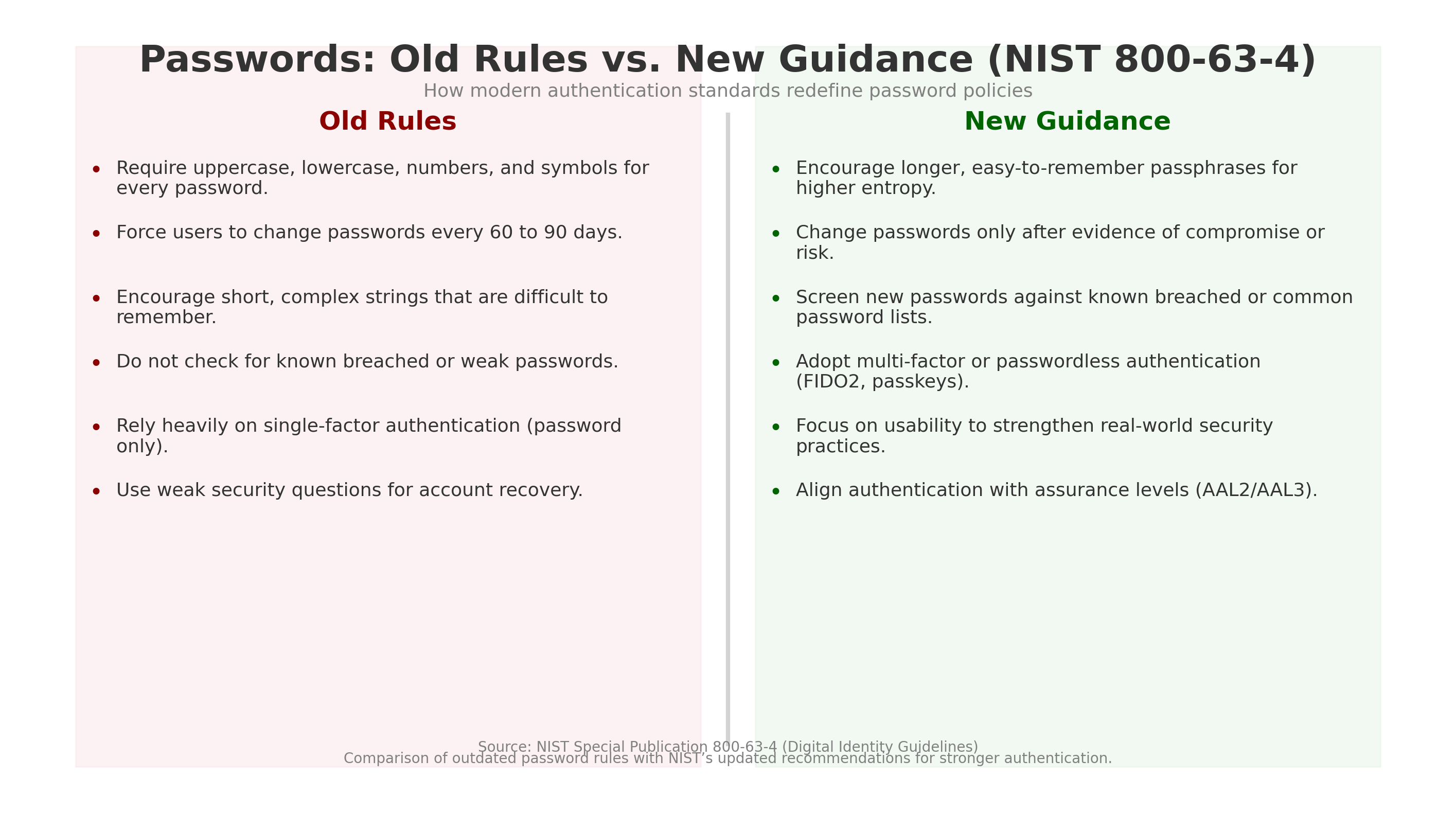 Comparison of traditional password policies and modern guidance from NIST 800-63-4.
Comparison of traditional password policies and modern guidance from NIST 800-63-4.
Why It Matters
These changes affect every stakeholder in the security ecosystem:
- Reduced Friction: Usability is now a design principle.
- Compliance Alignment: Federal agencies and contractors will soon adopt 63-4 as baseline guidance.
- Training Updates: Cyber educators must revise labs, awareness campaigns, and policy language.
- Zero Trust Alignment: Identity assurance now underpins access decisions across all systems.
Ultimately, the standard redefines security from “remember this string” to “prove who you are.”
Inside the Guideline: Identity, Authenticator, and Federation Levels
NIST introduces three dimensions to evaluate identity assurance:
- IAL (Identity Assurance Level): How rigorously a user’s identity is verified.
- AAL (Authentication Assurance Level): How strong the authentication process is (AAL1 through AAL3).
- FAL (Federation Assurance Level): How trustworthy identity data is when shared across domains.
These levels fit naturally into the Zero Trust mindset, which continually verifies identity, device, and context rather than relying on static credentials.
From Policy to Practice
How can you start aligning with 63-4 today?
- Enable MFA or passkeys in your identity platform such as Azure AD, Okta, or Keycloak.
- Stop enforcing arbitrary complexity requirements that frustrate users.
- Start screening passwords against known breach lists.
- Update acceptable-use policies and awareness training to reflect the new guidance.
TIP — Practical example:
In Keycloak, you can reach AAL2 compliance by enabling WebAuthn/FIDO2.
Users log in with platform authenticators like Windows Hello or Touch ID instead of passwords.
What Comes Next: The Passwordless Lab
Over the next week, we will put this guidance into practice in a new ProftSec project:
ETR: Implementing Passwordless Authentication with NIST 800-63-4
Using Keycloak and FIDO2, we will configure passwordless authentication and map it directly to NIST’s assurance levels, extending our Zero Trust lab environment.
Security Evolved
NIST 800-63-4 does not eliminate the password, it improves it.
The focus has shifted from memorization to measurable assurance and adaptive authentication.
Whether you manage enterprise systems, teach cybersecurity, or advise small businesses, now is the time to modernize your identity strategy and prepare for a passwordless future.
Resources
- Official NIST SP 800-63-4 Publication →
- Coming soon: [ETR: Implementing Passwordless Authentication with NIST 800-63-4]