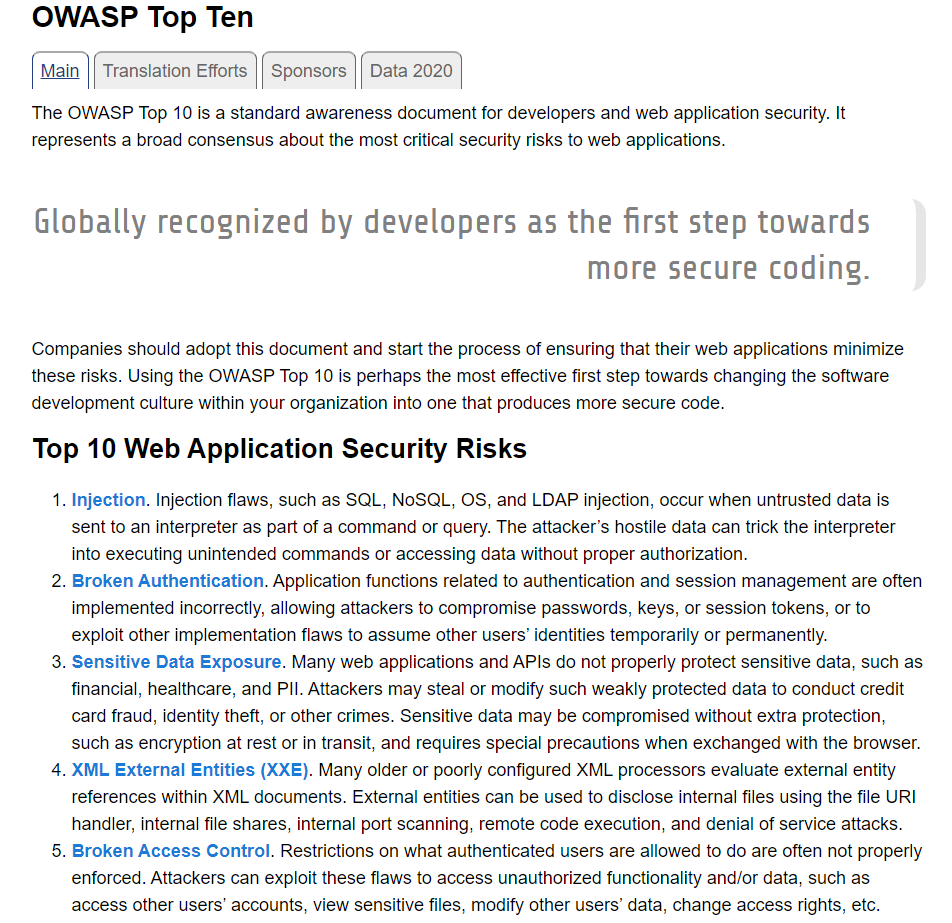
As you can see from their list, the number one item consists of different types of injections. These range from SQL Injections, Command Injections, Directory Transversals, Header Injections to Cross Site Request Forgery's. This project aims to give you a small sample of each of these injection types so you can see how they work first hand.

You will need the following to complete this assignment:
****Need to add here.****
Please be sure to create a Google Doc that contains screenshots with captions indicating what you are accomplishing. This will be used to help show that you completed the project and can be used as a reference later on for you. This will also be your submission for this project. The number of screenshots is to be determined but typically it should match the page count of the project.
Open up a web browser and head here Kontra OWASP Top 10 for Web
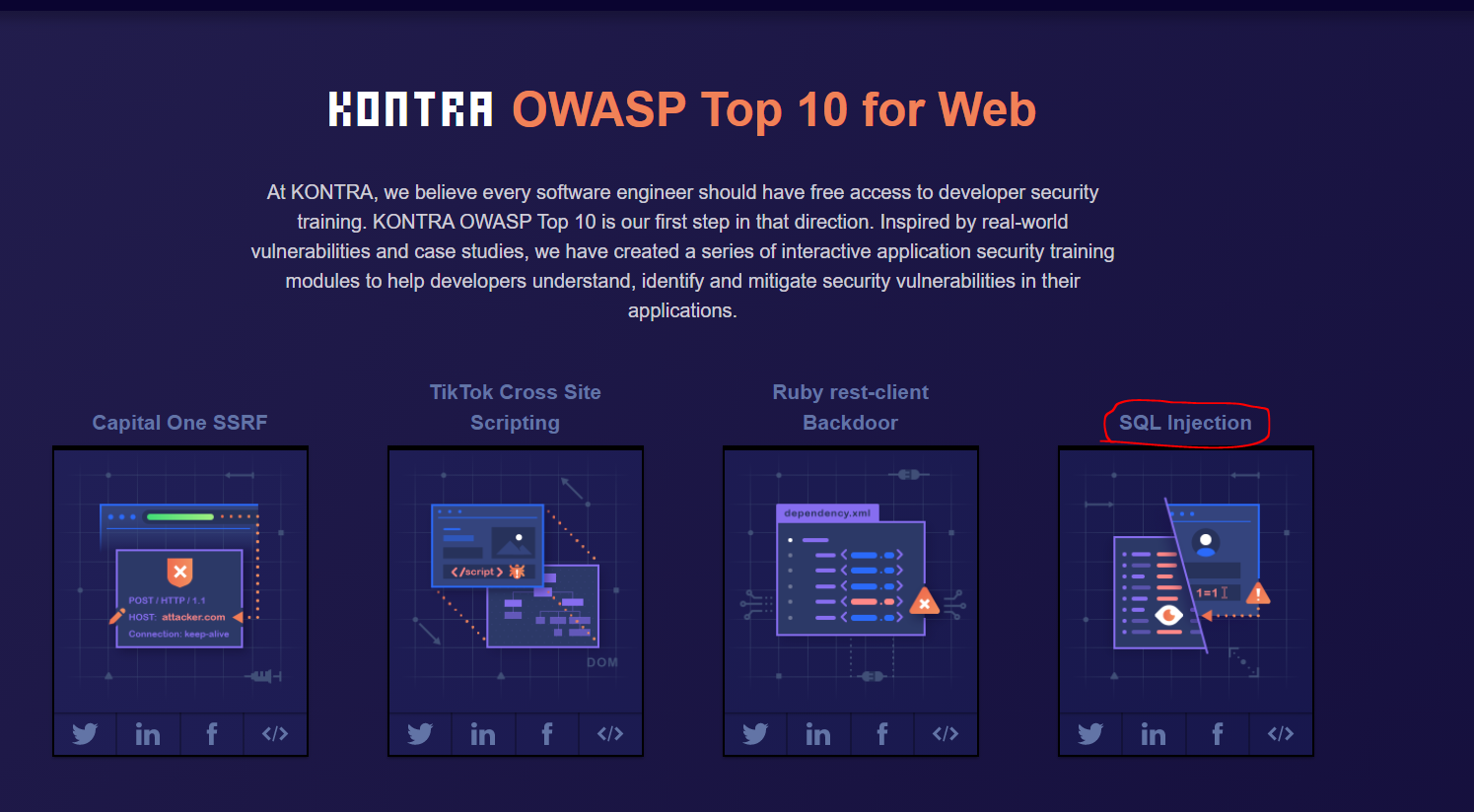
As you can see there are a number of available exercises. For this project, you will be working through the following:
For each of the exercises above, take screenshots (3-4) of each exercise as you progress through it. There should be a total of 15-20 screenshots for this.
Make sure to put an appropriate header dividing each of the exercises up. Write a small paragraph (think of a report) as you are completing each of these. Discuss in these paragraphs
what you are learning, if it was of value, and if you have any questions about the exercise that you are performing.
This concludes this project. PLEASE MAKE SURE YOU ARE SHUTTING DOWN YOUR VM EACH TIME UNLESS YOU ARE LEAVING IT RUNNING FOR A TASK IN THE COURSE.
Please make sure to submit your project as instructed by your instructor by it's due date and time.
References
New Project created Mar 2021
Updated directions for Apr 2022
OWASP Top Ten
Kontra OWASP Top 10 for Web