You will need the following to complete this assignment:
****Need to add here.****
Please be sure to create a Google Doc that contains screenshots with captions indicating what you are accomplishing. This will be used to help show that you completed the project and can be used as a reference later on for you. This will also be your submission for this project. The number of screenshots is to be determined but typically it should match the page count of the project.

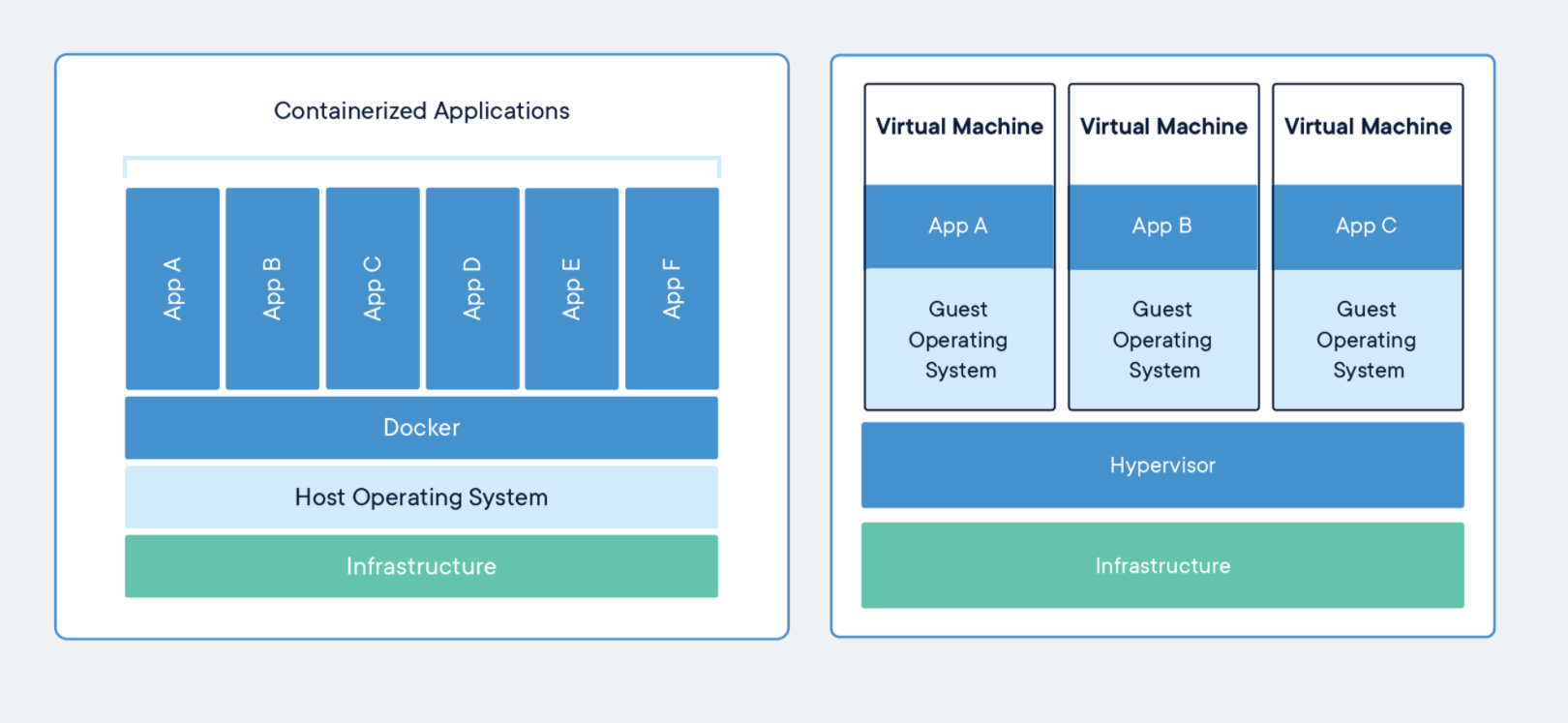
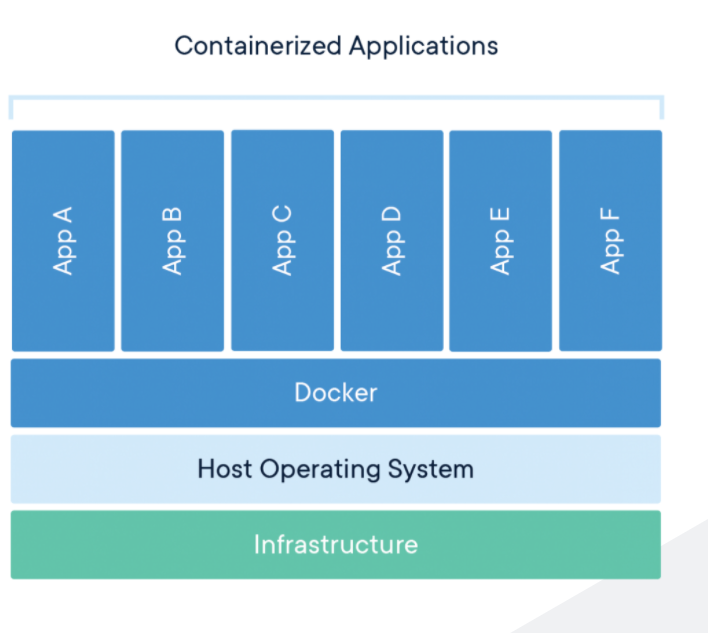
As you can see from the image above, what separates out Docker from VM's is that all applications share the Docker Engine as their main source, instead of VM's where each VM has it's own guest operating system. Again, I'd
recommend looking at this website for more information: What is a Container-Docker?
To get this project started, we need to set up Docker's repositories to have the ability to easily install the platform and handle upgrades. Again, this will be very similar to setting a repository for your Linux distribution where it goes and pulls updates for your Debian platform. Enter the following to setup the repository over HTTPS:
sudo apt update
sudo apt install apt-transport-https ca-certificates curl gnupg-agent software-properties-common -y
From here, we need Docker's official GPG key:
curl -fsSL https://download.docker.com/linux/debian/gpg | sudo apt-key add -
Now let's verify that we downloaded the correct file by searching for it's fingerprint. The fingerprint should be: 9DC8 5822 9FC7 DD38 854A E2D8 8D81 803C 0EBF CD88. We should be able to find it based on it's last 8 characters.
sudo apt-key fingerprint 0EBFCD88
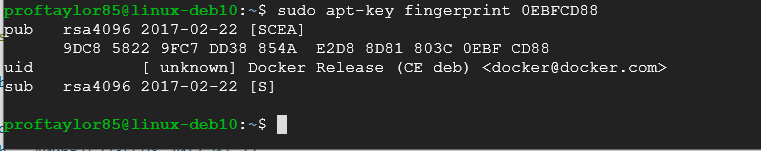
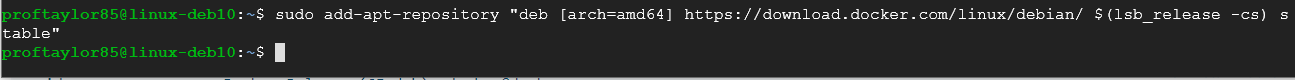
Now let's add a stable repository for Docker. We could use a nightly or a test repository but we want this to be have stability and hopefully no bugs.
sudo add-apt-repository "deb [arch=amd64] https://download.docker.com/linux/debian/ $(lsb_release -cs) stable"
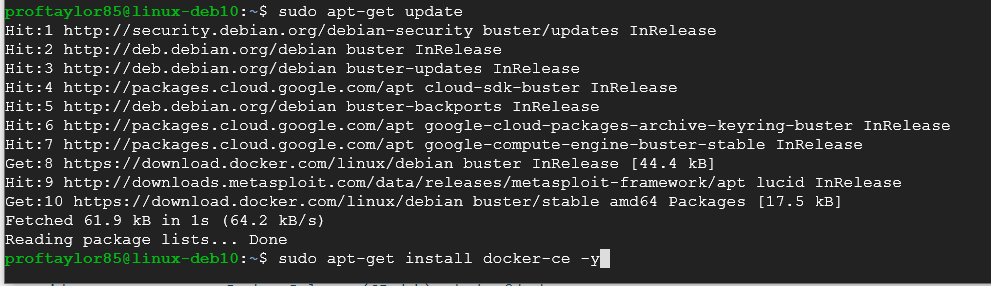
From here we need to apply any new updates that may impact the functionality of the Docker repository and then install the actual Docker daemon (a service process that runs in the background and supervises the system and typically provides functionality to a bunch of processes).
sudo apt-get update
sudo apt-get install docker-ce -y
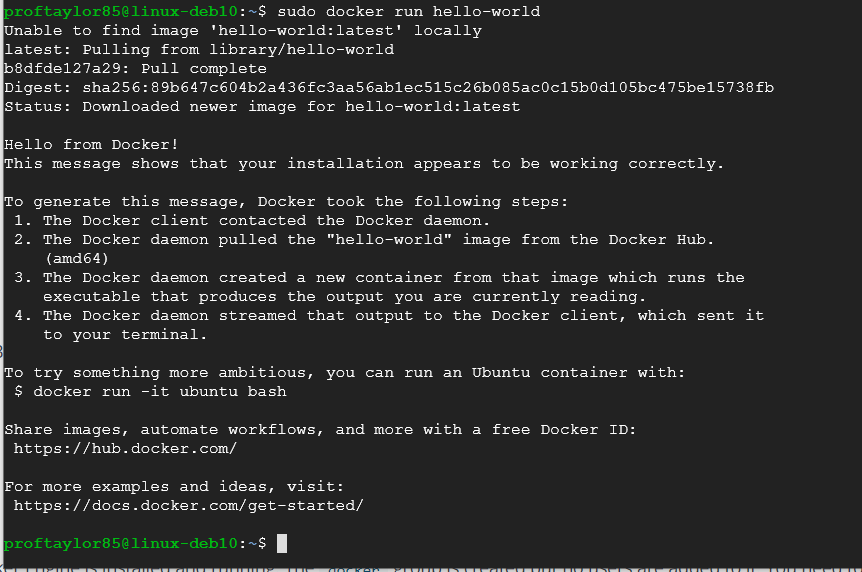
It may take a few moments for it to download and install Docker. Lastly, let's check to make sure we installed the docker container correctly. Docker has the classic "Hello World" example that we will use to our advantage. Type in the following:
sudo docker run hello-world
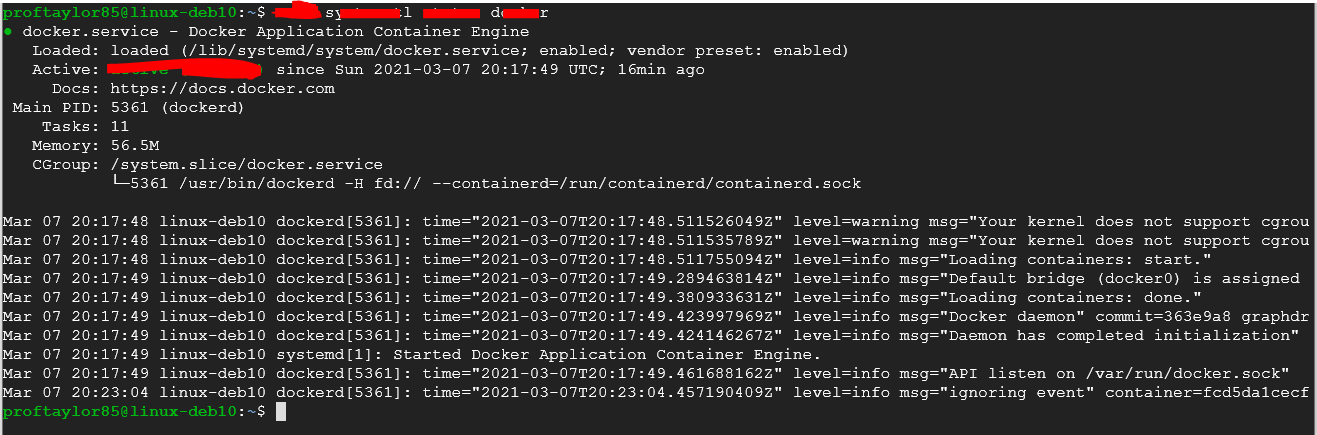
Another way to prove that Docker is running correctly would be to check the status of the program. To run this issue a command that looks at the 'systemctl status docker'. Please do NOT forget that you need root privileges to do this. Take a screenshot showing your command and the output. Use my image below for reference.
Now that we know that Docker is working correctly, let's go download our docker container of SSTI. According to Docker Hub/Container: SSTI_env we can also install it and run it with the second command below:
sudo docker pull dockerbucket/ssti_env
sudo docker run -p 60:60 dockerbucket/ssti_env python ~/vulncode.py
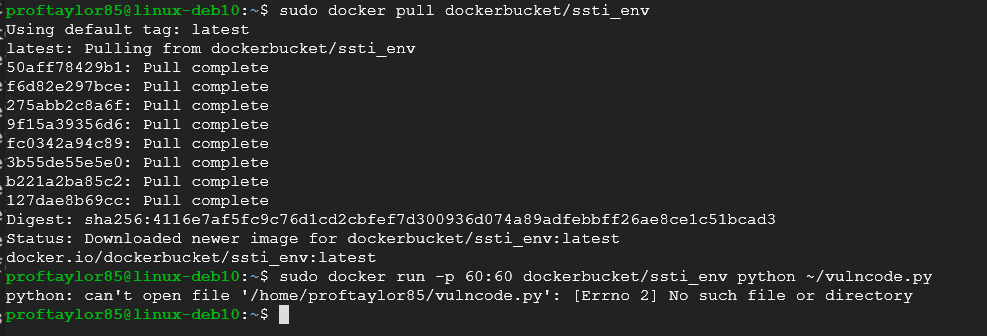
As you can see from the output above, the command directly from the website doesn't work. The reason for this, is that is because it is assuming you are the root account when you install the file/program/docker files. Let's modify it a bit to get it to work.
sudo docker run -p 60:60 dockerbucket/ssti_env python /root/vulncode.py
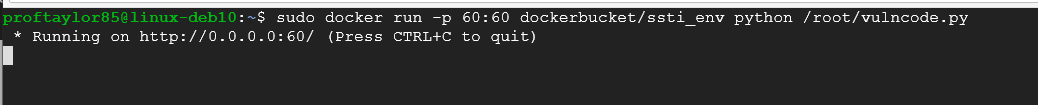
As you can see from the image above, the docker container is running on a localhost via port 60. **LEAVE THIS WINDOW OPEN IN ORDER FOR THE DOCKER CONTAINER TO RUN SUCCESSFULLY**
From here, go back to your Google Cloud Platform and click on the Navigation Menu ☰ go to Networking and find VPC network → Firewall. We need to add a rule to allow traffic on port 60 since this docker container requires it.
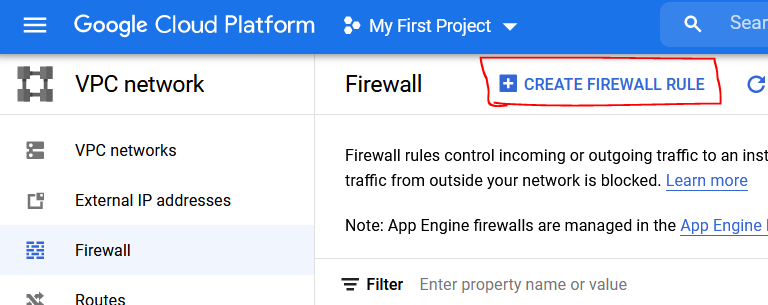
On this new window, you should see CREATE FIREWALL RULE (Refer to image above for assistance.) Click on this and add the following rule in:
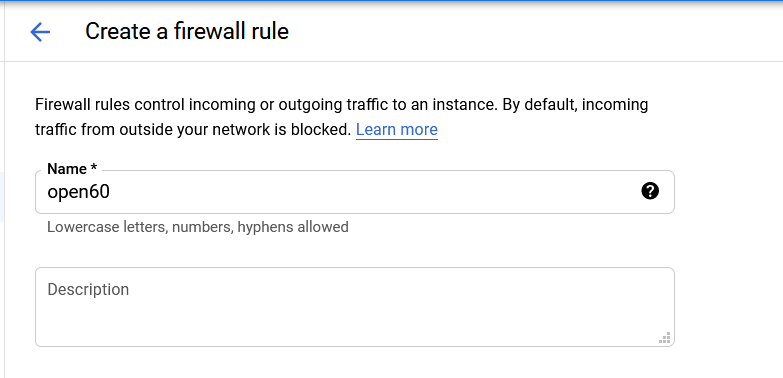
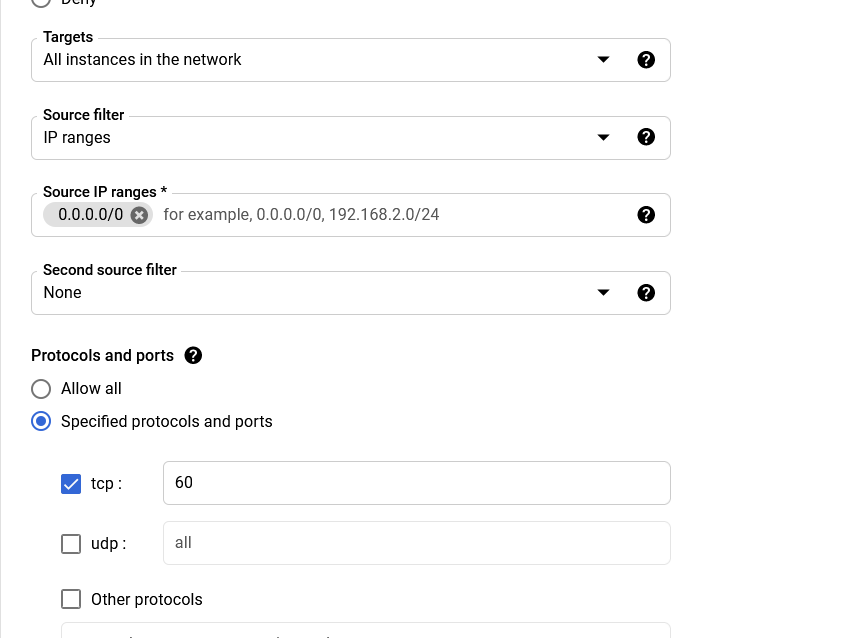
Click on CREATE at the bottom. This should return you to the Firewall page.
Take a screenshot and highlight your new rule shown the in the list of rules.
Now your system should be able to connect the vulnerable server running on your Docker instance. In order to this, you need the external IP address of your system. Go to the Navigation Menu ☰ , go to Compute and find Computer Engine → VM Instances. Find your External IP address and make note of it. Use my image below for reference.
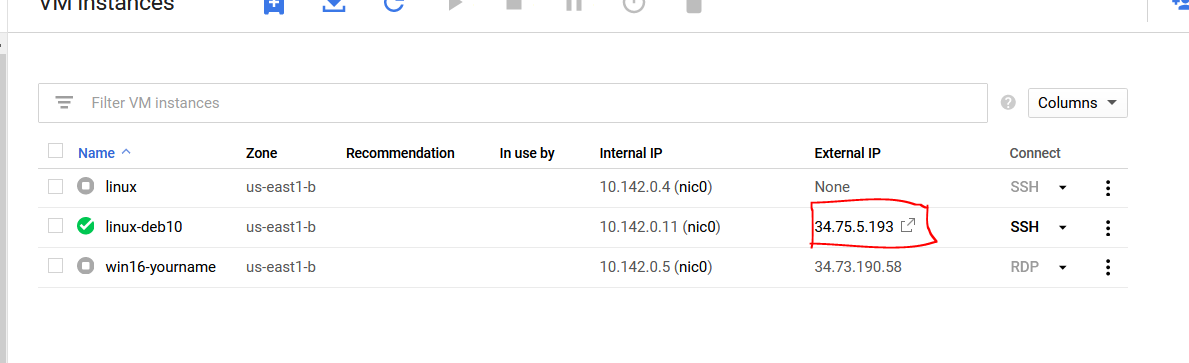
In a web browser, enter your IP address followed by :60. Again, use my example below for reference:
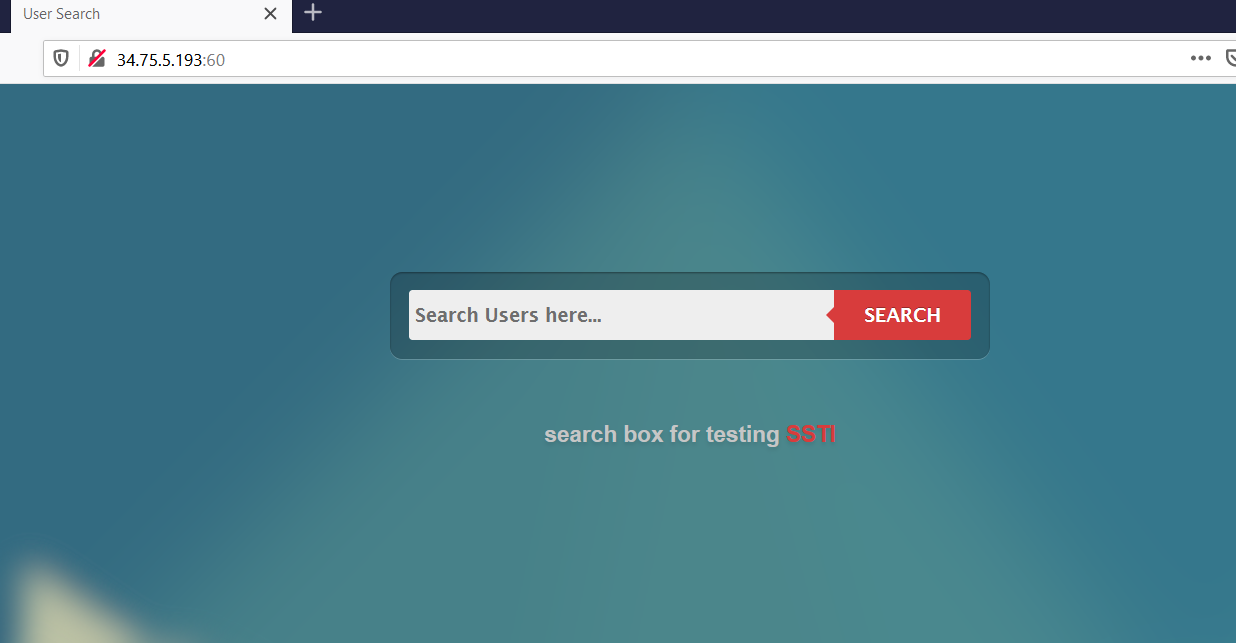
Take a screenshot showing that SSTI box is reachable via a web browser. Use my image above for reference.
You are now ready to explore the topic of Server-Side Template Injection. To begin with, let's set the stage for what you are about to do. Server-side template injection is when an attacker is able to use native template syntax to inject a malicious payload into a template, which is then executed server-side.
Template engines are designed to generate web pages by combining fixed templates with volatile data. Server-side template injection attacks can occur when user input is concatenated directly into a template, rather than passed in as data. This allows attackers to inject arbitrary template directives in order to manipulate the template engine, often enabling them to take complete control of the server. As the name suggests, server-side template injection payloads are delivered and evaluated server-side, potentially making them much more dangerous than a typical client-side template injection.
Let's see a normal query in action. In the search box, type in your first name and click on SEARCH.
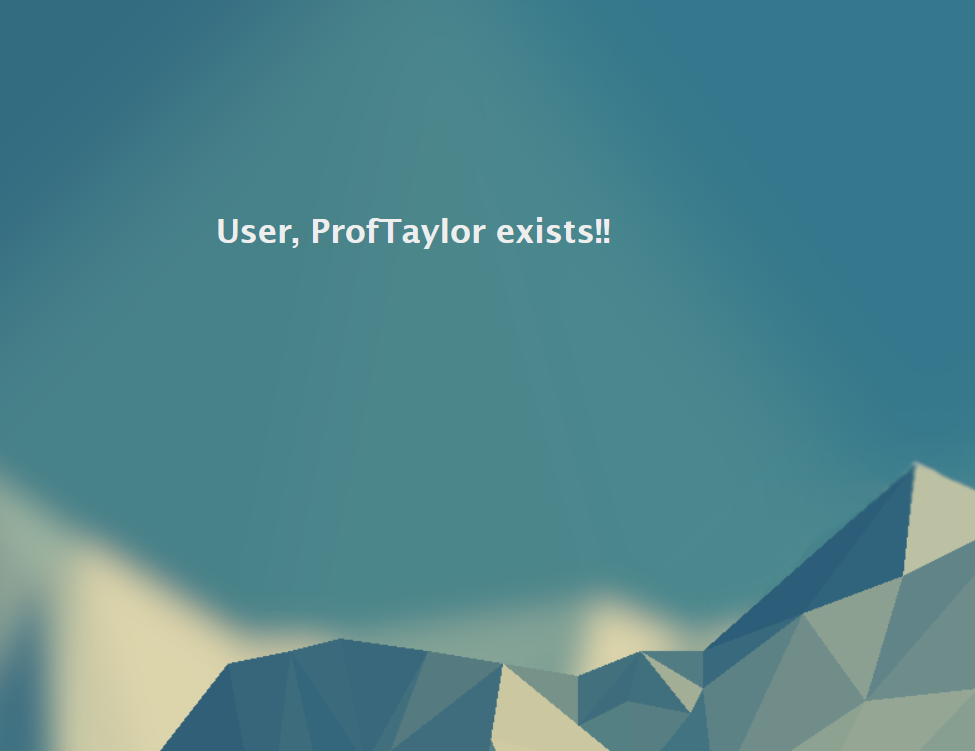
Take a screenshot showing your name from the search query. Use my screenshot from above for reference.
Click on the back button to go back to the search query. Let's find out if the search box will actually perform an expression instead of just reading a string text. Enter the following and click on SEARCH:
{{3*3}}
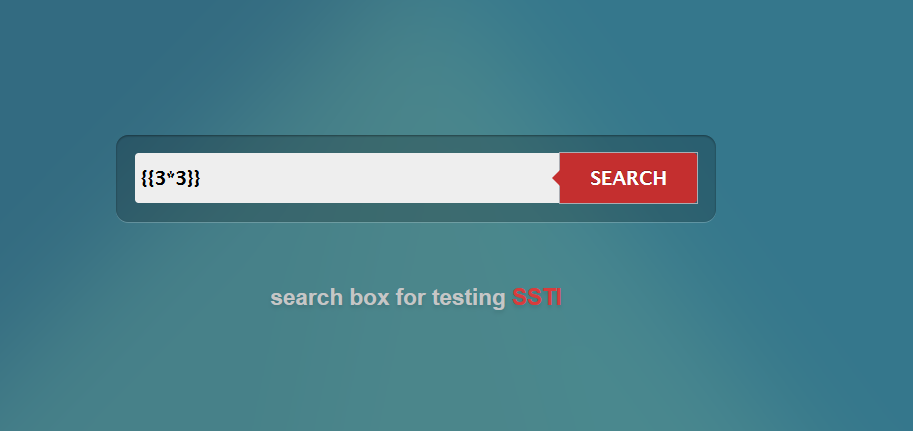

Uh-oh. We have a problem here. The server has executed the expression on the server end.
To further explain the impacts of Server-side template injection vulnerabilities, they can expose websites to a variety of attacks depending on the template engine in question and how exactly the application uses it. "In certain rare circumstances, these vulnerabilities pose no real security risk. However, most of the time, the impact of server-side template injection can be catastrophic.
At the severe end of the scale, an attacker can potentially achieve remote code execution, taking full control of the back-end server and using it to perform other attacks on internal infrastructure.
Even in cases where full remote code execution is not possible, an attacker can often still use server-side template injection as the basis for numerous other attacks, potentially gaining read access to sensitive data and arbitrary files on the server." Portswigger: Server-side-template-injection
To further illustrate this, let's use this decision tree from the Portswigger site:
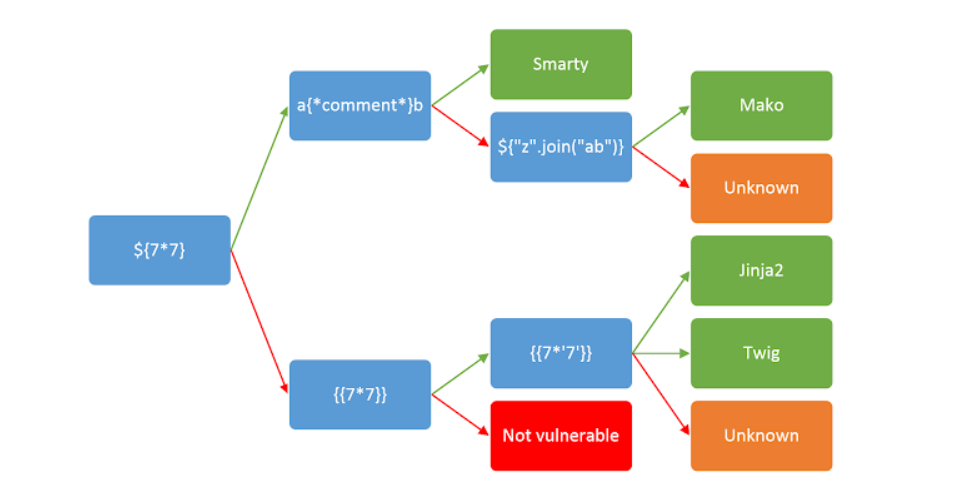
The blue colored boxes indicate different strings you can try in the search queries. If they are successful, follow the green arrow; otherwise, follow the red arrow if they do not work. Let's start with the first expression:
${7*7}
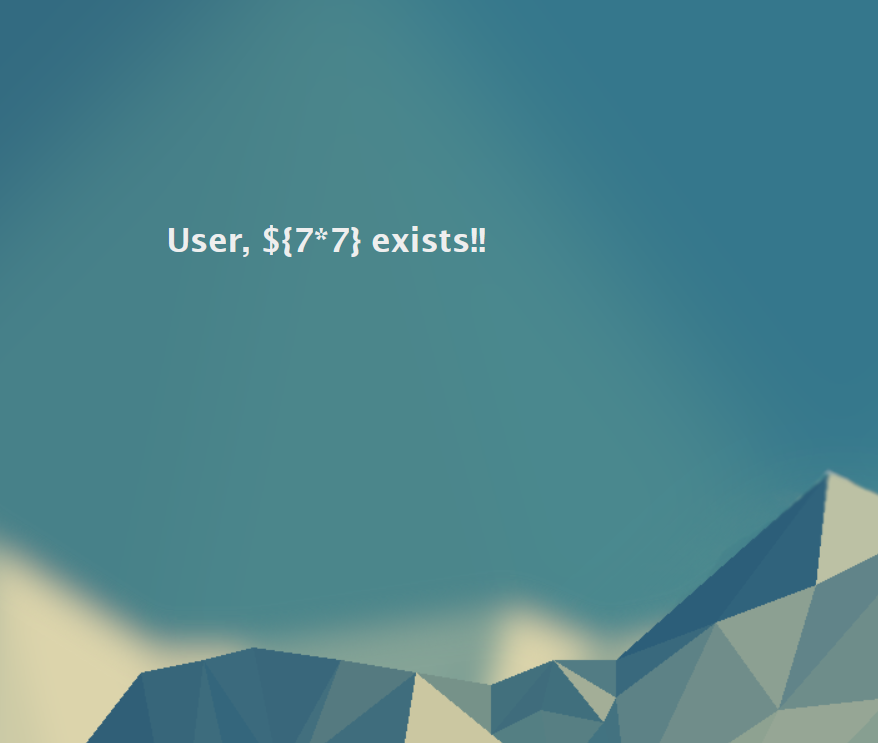
As we can see from the result, the expression does not work, so to the bottom blue box we will go. Let's try that one:
{{7*7}}
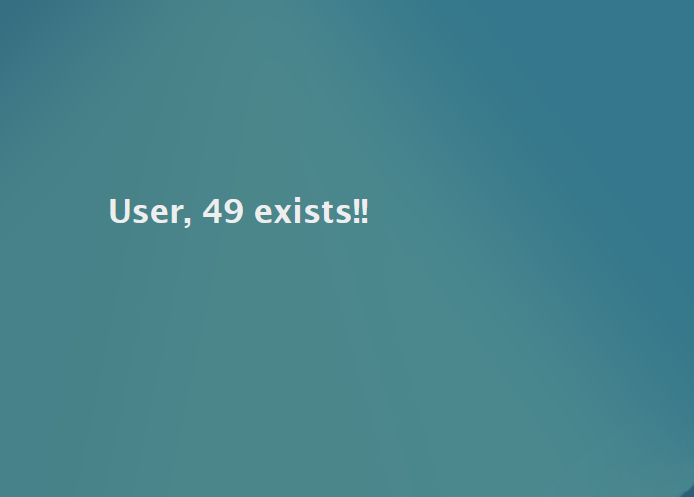
This one was successful, so follow the green arrow to the next blue box:
{{7*'7'}}

The results shown could take us in one of two directions depending on what is shown. If the results shown are 49, then the server is using Twig as it's template language. If the results are 7777777, then Jinja2 is the template language being used.
Take a screenshot of the results. Indicate which platform is being used.
From here, we will move into the next project which will look at Inheritance of class objects and how they can work in conjunction with SSTI.
This concludes this project. PLEASE MAKE SURE YOU ARE SHUTTING DOWN YOUR VM EACH TIME UNLESS YOU ARE LEAVING IT RUNNING FOR A TASK IN THE COURSE. Please make sure to submit your project as instructed by your instructor by it's due date and time.
References
What is Docker?
Install Docker on Debian
Docker Hub/Container: SSTI_env
Portswigger: Server-side-template-injection